One of a small company’s biggest cybersecurity vulnerabilities is its user passwords. Passwords are often the only thing guarding volumes of company data stored in cloud solutions and they leave companies at risk for a couple of key reasons.
- Bad password habits: Users tend to use weak passwords, store them in unsecured ways, and reuse the same password multiple times.
- Breaches of large databases of passwords have become common.
The necessary move to using cloud technologies for business continuity and the rise of the remote workforce have both led to data security challenges for businesses that don’t have a good access management strategy.
80% of organisations have suffered at least one cloud account breach within the past 18 months.
One particularly tough password problem to solve is that even if you require the use of strong passwords at your company, data breaches of large social platforms and online retailers are common these days. This means that a password your team has used on another site could be stolen from that site’s database of user passwords.
Those username and password combinations then end up for sale on the Dark Web. Compounding this issue is that users tend to reuse passwords across multiple accounts, so one password breach of this type could endanger several online accounts.
In 2020, security experts found that 500,000 stolen Zoom passwords were being sold on Dark Web criminal marketplaces.
We’re not in a time yet where passwords aren’t vital for the everyday workflow, so it’s important to protect them. One of the best ways to do this is through the use of two-factor authentication (2FA).
Things to Think About When Implementing 2FA
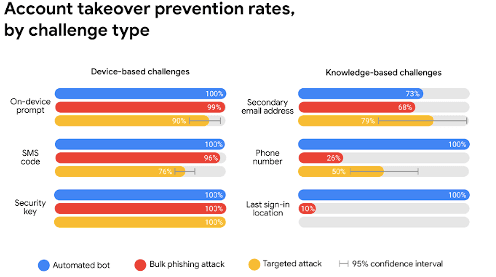
Two-factor authentication can block between 76-100% of fraudulent sign-in attempts, depending upon the method being used. It’s so effective because it requires a specific physical device to be in the user’s possession to complete the login.
The most common form of 2FA is for a site to send a user a code after they enter their username and password. The code is sent to a specific device. The user inputs that code to complete the login.
The code is typically:
- 6-8 characters in length
- Time-sensitive (expires in 5-10 minutes)
- Unique for each login attempt
If a hacker doesn’t have access to the device that receives the code, they’re locked out, even if they have the correct username and password combination.
In today’s environment that includes higher threats to user passwords than ever before it’s vital to enact 2FA on all your logins. But it does need to be done thoughtfully.
Here are some things to consider for 2FA implementation to go smoothly.
How Many Logins You Need to Switch to 2FA
Implementing 2FA can be an easy decision for cloud security, but it’s not hard for a company to miss an account or three if they don’t have an organised plan.
It’s important to list out all company accounts that require a login, which can be quite a few. The average small business (less than 50 employees) has approximately 40 different cloud apps in use.
You also need to consider other types of logins like Remote Desktop Protocol (RDP), which may be being used by work-from-home employees to access on-premises servers or desktops.
List out all logins your company uses so you can put together a plan to have all of them secured by 2FA.
Consider a Single Sign-on (SSO) Solution
One thing that holds companies back from implementing two-factor authentication is that employees complain that it will slow them down. If they have to log in to several different work apps a day, they may worry about spending extra time retrieving and inputting a 2FA code for them all.
A single sign-on solution can alleviate this issue. It connects to all your accounts and allows employees one login portal to access them. So, employees can log in and use 2FA once to reach all their cloud accounts. This enables 2FA security without having it drag down productivity.
How Is Everyone Going to Receive the 2FA Code?
You might think that one form of 2FA is as secure as another, but that’s not quite the case. While all methods can offer significant protection against fraudulent sign-in attempts, they do have slight security differences.
The three main ways to receive a 2FA code are:
- Via SMS/text message (most common)
- Via on-device prompt in an authentication app
- Via a security key (most secure)
In a Google study on two-factor authentication methods against three major types of attacks, it was found that SMS was the least secure (76-100% effective). This is because mobile SIM cards can be cloned.
The most secure was using a security key, which is a small device you purchase that plugs into your phone or computer to authenticate the 2FA login. This method blocked 100% of all account attacks.
Receiving an on-device prompt in an authentication app was in the middle, blocking 90-100% of attacks.
Need Help Implementing a 2FA Plan for Your Small Business?
NMX IT Solutions can help your Thames Valley area company implement a smart and convenient 2FA strategy to significantly improve your cloud account and remote login security.
Contact us today to schedule your consultation! Call 01628 232300 or reach out online.

